It’s not a coincidence that the Beltug panel of IT-leaders mentions cybersecurity as their number one priority for 2023. In a world that is becoming increasingly complex and dangerous, the number of cyber threats is rising, and attackers are becoming better at cracking systems. No one knows how sophisticated these cybercriminals are going to get but anticipating is key for your organization. Here are 5 key areas we believe you need to monitor closely as a CISO or DPO.
Cybercrime is booming business
The number of Cyber attacks is not likely to diminish any time soon, although no one knows with 100% certainty what the evolution will look like. Nevertheless, some trends are appearing for example, it seems that the number of attacks in the first half of 2022 have increased by more than 40% compared to last year, with Ransomware representing the biggest threat to businesses. These types of attacks cause severe disruptions and often have far-reaching consequences for businesses.
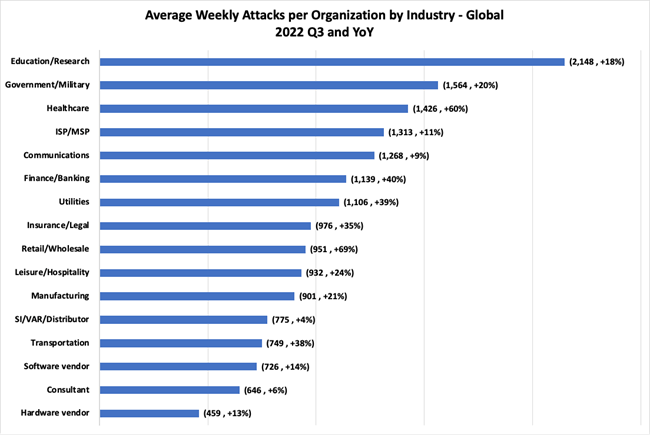
"It appears that attacks have increased
by more than 40% compared to last year."
Key area 1: User Awareness
More than 90% of workers who have access to the Internet are NOT able to
spot a fraudulent phishing email. This explains why phishing and its variants
remain a popular and efficient tool for cybercriminals. Additional research
shows that 80% of attacks can be stopped by practicing good cyber security hygiene.
Through targeted training, we can create awareness among employees about
these types of attacks and how to recognize them. The message is clear: as a company today, you should not only invest in a technical solution to protect
against cyber-attacks, but also train employees on the right skills. In short, you need to build a human firewall.
Key area 2: Mobile device policies / endpoint security
About 2/3rds of the world's population uses a smartphone. These devices are
part of our daily lives and contain personal data, bank details, passwords and
even health data. Consequently, they have quickly become the hackers highway
to access sensitive data. Types of attacks include ‘smishing’, but also the use of malicious apps that slip through the cracks of the security checks in the
App Stores.
In addition to smartphones, the popularity of laptops has also skyrocketed.
With all these devices and working from home no longer being the exception, companies need to provide significantly reinforce their endpoint security
efforts, as work is no longer always done within a "secure" corporate network.
Key area 3: Cloud Security
Now that remote work is fully established, the demand for Cloud solutions is also rising. Companies are moving their data storage to the cloud – including their sensitive data. While the advantages of the cloud are obvious, a downside is that many cloud solution providers do not offer encryption or secure authentication, putting companies back in the crosshairs of hackers.
SaaS providers will also have to step up their game and take responsibility, since users don’t have much to say in terms of the security or even the storage location of their data. Cloud security and avoiding ransomware attacks, certainly deserves extra attention in 2023.
Key area 4: Data Privacy
The General Data Protection Regulation protects the personal data of European consumers since 2018 and applies to European companies and, by extension, all companies trading with Europe. We see that the principles behind it are now trickling down to other parts of the world as well.
In sum, this fairly recent legislation is impacting many businesses, often without being fully embedded in all processes. Further investments will therefore continue to be necessary in 2023, with Data Loss Prevention Systems as one of the main focuses from a cybersecurity perspective.
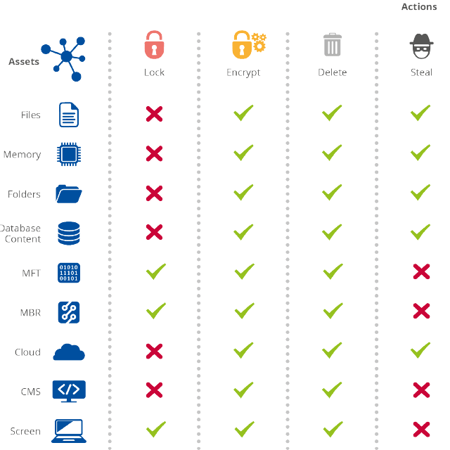
Fig 2. ENISA - Possible Actions Performed by 'Asset' by Current Ransomwares
Certain sectors are particularly susceptible to cyber attacks due to the volume and type of data they work with. The banking & financial sector come to mind, but so does the healthcare sector. Hospitals are committed to protecting their patients' data. A data breach is therefore the number one threat for the healthcare sector. This sector experienced one of the largest increases in attacks in H1 2022 and that will only increase in 2023 (see fig 1. Trends Healthcare).
In the same way, GDPR-compliance continues to be a strong focus in many organizations. And with good reason: analyses by ENISA show that 58.2% of
stolen data includes personal data.
Key area 5: IoT
There are reportedly already 7 billion "Internet Of Things" devices currently connected to the Internet. And that number, according to experts, will triple
by 2025. Almost every electronic device you can buy today can connect to the Internet.
Manufacturers aim for mass production with the lowest possible product
and manufacturing costs. Security is then often given less attention.
The same hardware and software are used for different products, by different manufacturers. As a result, a single vulnerability can have an enormous impact
on multiple products.
So, as the number of IoT devices continues to grow exponentially in the coming years, so will the threat that a hacker will exploit such a vulnerability to gain
access to a corporate network.
Curious how we can help you protect your critical infrastructure?
Submit your info below and we'll contact you asap.




